(Source: https://unsplash.com/photos/vBCVcWUyvyM)
Initially emerged as a platform to exchange digital currency over the Internet, blockchain technology is now a general-purpose platform for business. Due to its potential applications in various Fields, the UN has included it as one of the frontier technologies to realize SDGs. Development engineers can understand the necessity of blockchain technology by knowing the Internet's potential and pitfalls as a business platform.
Why Blockchain Technology
The Internet has introduced an information-centric business model, and it has revolutionized the way people transact online. For example, the emergence of e-commerce sites (e.g., Amazon) has been attributed to the growth and widespread presence Internet.
The Internet has bridged the information gap between goods provider and goods consumer by creating third-party information intermediaries called service providers. These agents, which are e-commerce sites, hold the information about who sells what, i.e. seller's information and who wants what, i.e. buyers profile and their needs — thus bringing together consumers of goods with that of producers.
The advantages of doing online business are that it simplifies the process of business transactions, reduces the time required for businesses, and as a result, it has brought prosperity to society.
In terms of SDGs, the Internet as a platform for business has created various opportunities for decent work and economic growth. The Internet as a platform for communicating information has reduced the impact of natural disasters such as cyclones and the spread of epidemics by timely disseminating useful information. The Internet as a learning platform has increased the accessibility of education, fostering education for all.
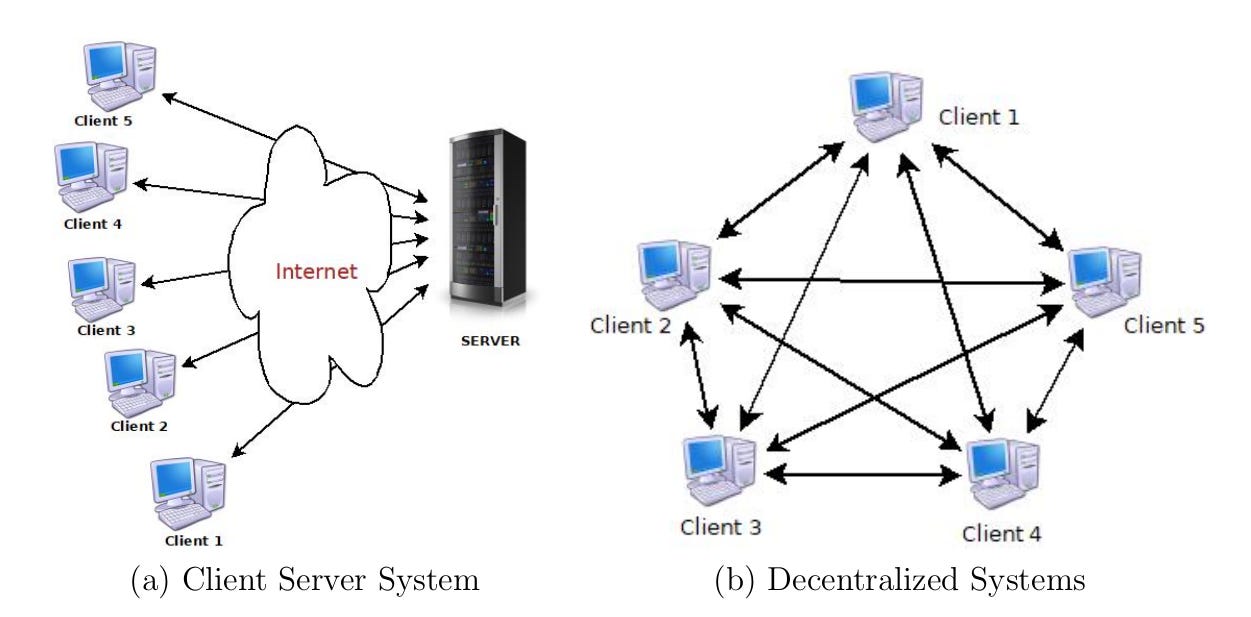
Despite the various benefits of the Internet, it has always remained an unreliable platform to share valuable personal information because of its mediator-centric or client-server model for information exchange. A server or mediator may be a payment gateway or an e-commerce site. The information shared with such sites is always susceptible to breach of security and privacy attacks.
The emerging blockchain technology removes these pitfalls by laying a trust layer on top of the existing Internet technology. It replaces the mediator-centric model of information exchange with the peer-to-peer model or decentralized model, as shown in Figure.
It transforms the Internet into a trustworthy platform for doing business when transacting parties do not trust each other. It eliminates the role of the mediator responsible for authenticating the identities of transacting parties.
Main Elements of Blockchain Technology
This section provides an overview of blockchain's essential elements and achieves the various quality attributes that make it one of the promising technologies. One can understand blockchain technology at the conceptual level and specific instance level. Bitcoin, Ethereum, and Hyperledger are a few common examples of specific blockchain. This section describes blockchain technology at the conceptual level. The four fundamental concepts common across the blockchain implementation are
Distributed Ledger,
Cryptography,
Consensus Protocols, and
Smart Contracts
Distributed Ledger
In a conventional sense, ledgers are the registers or logbooks employed for account-keeping or book-keeping operations. Similarly, in the context of a blockchain-based information system, ledgers are the databases storing up-to-date information about business transactions. These are distributed among all the nodes participating in the network. In a blockchain environment, ledgers are not stored in a central place. They are distributed among all the nodes. So multiple copies of a ledger exist in a business network. Hence these are referred to as distributed ledgers. When a node in a network updates its local copy, all other nodes synchronize their copy with the updated one. Hence, each copy is consistent with the other.
These ledgers are used to store information about valuable assets. In the Bitcoin implementation, the first blockchain-based system, ledgers, are used to store digital currencies. One may use it to store information about other valuable assets such as land records, diamonds, student's academic credentials and others.
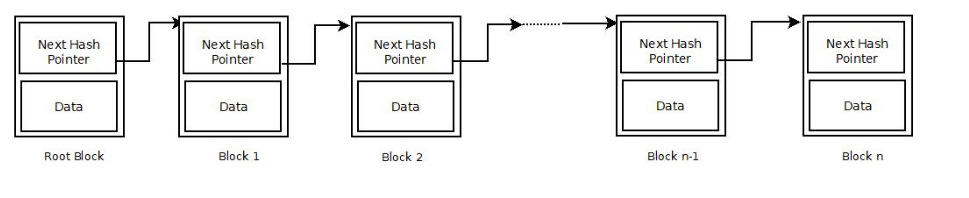
In a blockchain-based information system, records in a distributed ledgers are arranged in a chain format, as shown in the above figure. Here, multiple transactions related to an asset are grouped in a block. The (n+1)th block in the chain links to the nth block, and the nth block links to the (n-1)th block and so on. The first block in a chain is called a genesis block or the root block. Due to this peculiar storage arrangement, the distributed ledgers are also known as Blockchain. It is worth noting that all blockchain-based systems contain distributed ledgers, but not all distributed ledgers employ blockchain-based storage mechanism. The blockchain data structure permits only append of new records. Updating and deletion of records are not permissible.
The most critical design feature of a blockchain-based information system is the use of hash pointers instead of physical memory based pointers to link blocks in a chain. A hash pointer is a message digest calculated from the information content of a block. Whenever a node attempts to tamper with the information content, a small change in the information leads to a ripple effect of changes in hash-pointers — making it impossible to change the information once recorded in the blockchain.
Facilitating mediator-less business transactions and supporting immutability of stored information are the two significant quality attributes of blockchain-based information systems. These quality attributes are derived from replicating ledgers on all the nodes in a network and linking blocks in a chain through hash pointers.
Typically, blockchains are of two kinds based on how blockchains are accessed, i.e. private and public blockchains. In a public blockchain, any node can join and leave the network and validate the business transactions. While in the case of a private blockchain, the network is small and requires permission to join and leave the network. Hence private blockchains are also known as permissioned blockchain, and public blockchain is known as a permissionless blockchain. For example, Bitcoin is a public blockchain, and Hyperledger is an example of a private blockchain.
Cryptography
Blockchain technology makes heavy use of cryptographic functions to assure trust among the users transacting over a blockchain-based business network. A typical business network includes many untrustworthy elements. In a conventional banking domain, an agent issuing the check without having sufficient balance in the account or an agent forging a signature are typical examples of malicious acts. In a digitized economy, these challenges are aggravated because of information transfer over an unreliable communication medium. Hence, cryptographic functions, a set of mathematical functions, are used to encode messages to assure information security in a network containing malicious or untrustworthy agents. These cryptographic functions address various purposes. Some of them are:
Authenticating the identity of agents involved in a business transaction: Blockchain-based systems use a kind of asymmetric key cryptography. These protocols use two different keys called public and private keys. The public keys are open and used as addresses for performing business transactions, while private keys are secret and used for validating the transactions. SHA-256 (e.g., Bitcoin) and ECDSA (e.g., Hyperledger) are some of the cryptographic protocols used for this purpose. The private blockchain use another service called membership service, which authenticates the identity for business transactions.
Cryptographic functions such as digital signature are also used to authenticate a particular transaction.
Ensuring Privacy: Maintaining the privacy of transactions is a challenge, especially in public blockchains (e.g., Bitcoin). In such systems, transactions are possible to trace to real-life identities. Advanced cryptography-based techniques such as cryptographic mixers (e.g., Zerocoin) and Zero-Knowledge proof (e.g., Zerocash) have been found useful to address this challenge.
Consensus Protocols
In decentralized systems, agreeing upon the global state of the transaction is a challenge. This is not an issue in a centralised system because only one copy of transaction history is present at the central authority (e.g., Banks main Server machine). Blockchain being a decentralized system holds multiple replicas of transactions at several nodes. Agreeing upon the unique state of the transaction is an issue that is solved by executing a consensus process involving all the nodes in the system. This process is typically carried out in three stages. In the first phase, a node is elected/selected as a leader node to decide upon a unique state. In the second stage, transactions are validated. In the third stage, transactions are committed. A variety of consensus algorithms exists in the blockchain-based system. These are often compared based upon how scalable the algorithm is and several malicious nodes it tolerates. The Proof-of-Work (PoW) algorithm used in Bitcoin is one example of the consensus protocol. It selects the leader node responsible for deciding upon a global state by solving a cryptographic puzzle. It takes about 10 minutes for solving the puzzle requiring extensive computational work and much electric energy. It can work in the presence of 50% of malicious nodes in the network.
The Proof-of-Stake (PoS) is another consensus protocol in which a leader is selected with the network's highest stakes. It has been found as scalable compared to PoW, and it also works in the presence of 50\% of malicious nodes in the network.
The Practical Byzantine Fault Tolerant (PBFT) is the third example of a consensus protocol that has been found scalable and works in the presence of 66% or 2/3 malicious nodes in the network.
Smart-Contracts
Smart contracts are the most significant element in the blockchain-based system because it configures such systems' behaviour. Blockchain programmers can customize the working of blockchain systems by writing programs called {\em Smart-Contract}. Smart contracts are scripts that are executed when a specific event occurs in a system. For example, in Bitcoin, a coin may be released when more than one signatures are validated or when miners solve a cryptographic puzzle.
Programmers can write these scripts in a native language provided by blockchain systems or general-purpose programmable language. For example, Bitcoin provides a simple and less expressive native language to write a smart contract, while Ethereum provides a Turing complete native language called Solidity to write smart contracts. In Hyperledger, blockchain programmers can write a smart contract in a general-purpose language such as Java/Go.













Blockchain Technology